In the rapidly evolving digital landscape, cybercriminals are constantly finding new ways to trick unsuspecting users into giving away their sensitive information. One increasingly common tactic is the use of masked domains—web addresses that closely resemble legitimate ones but are controlled by malicious actors. In this blog post, we will shed light on how masked domains work, provide real-world examples of how they’re used to deceive people, and offer practical advice on how to spot and avoid these scams. This is a critical security warning for our clients and the public to stay vigilant and safeguard against credential theft and other cybercrimes.
What Are Masked Domains?
Masked domains impersonate or closely mimic legitimate domains to deceive users. They range from subtle misspellings to completely different extensions or subdomains. For instance, a scammer might replace an “m” with an “rn,” or switch “.com” to “.co,” making it difficult for the average user to distinguish them from the real thing.
General Examples:
- Legitimate:
www.example.com - Masked:
www.exarnple.com(using “rn” instead of “m”) - Legitimate:
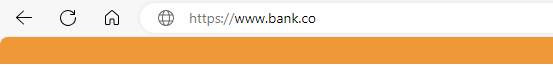
www.bank.com - Masked:
www.bank.co
E-mail Example:

Web Browser Example:
When done effectively, users may unknowingly interact with forged e-mail addresses or websites, which generally leads to information leaks or credential theft.
What Are The Risks?
Masked domains are often created by cybercriminals aiming to:
- Steal Credentials: Trick users into entering their login details on fake login pages. They then use these credentials to access your systems and data.
- Phish for Information: Collect personal and financial data through deceptive forms.
- Distribute Malware: Make users download malicious software disguised as legitimate apps or files. Once installed or activated, they leverage your system to gain access to additional systems and information.
- Impersonate Organizations: Pose as trusted entities to solicit money, data, or influence.
These actors range from individual hackers to organized crime rings and even state-sponsored entities. The risks can be severe.
The methods used to trick people include:
- Phishing Emails: Fake emails that appear to come from a legitimate source, directing recipients to a masked domain.
- Example: An email seemingly from your bank, asking you to verify your account at a URL like
www.bank.coinstead ofwww.bank.com.
- Example: An email seemingly from your bank, asking you to verify your account at a URL like
- Typosquatting: Domains registered with common typos of popular websites.
- Example: Registering
www.faceb0ok.cominstead ofwww.facebook.com.
- Example: Registering
- Homograph Attacks: Using characters that look similar to the original, like Cyrillic letters or accented characters.
- Example: Using
рaypal.com(with a Cyrillic “р”) instead ofpaypal.com.
- Example: Using
- Subdomain Impersonation: Creating subdomains that seem to belong to a legitimate organization.
- Example:
paypal-security.example.com.
- Example:
- URL Shorteners: Hiding the destination domain behind a shortened URL.
- Example: Using
bit.ly/abc123to redirect to a malicious site.
- Example: Using
Real-World Examples
- PayPal Scam:
- An email pretending to be from PayPal directed users to
security-paypal.com, which looked like the genuine site but stole login credentials.
- An email pretending to be from PayPal directed users to
- Apple Phishing Attack:
- A fake Apple ID verification email sent users to
appleid.apple.com.co, a masked domain set up to collect login details.
- A fake Apple ID verification email sent users to
- Government Scam:
- A masked domain like
gov-payment-update.comwas used to impersonate a government agency, tricking users into providing their Social Security numbers.
- A masked domain like
- MSP Impersonation:
- An e-mail that looks like support@sirkit.ca that is actually from support@sirk1t.ca. The technician requests remote access to help with a support or security issue.
How to Identify and Protect Against Masked Domains
- Double-Check URLs:
- Train your team to review and verify the website URL before entering sensitive information
- Be wary of subtle typos, extra characters, or strange extensions
- Inspect Links and Addresses in Emails:
- Train your team to hover over URLs/links to reveal their destination
- Train your team to review the e-mail address carefully for accuracy
- Only use trusted and confirmed links and e-mail addresses
- Use Two-Factor Authentication (2FA):
- Enable 2FA wherever possible to add an extra layer of protection
- Report Suspicious Domains:
- If you suspect a domain is being used maliciously, report it to the legitimate organization or relevant authorities
- Educate Employees and Family:
- Ensure everyone in your organization or household is aware of these scams
- Security Tools:
- Use e-mail services and security tools that actively monitor for masked domains
- Activate Microsoft Defender for Office 365 to verify links are safe
- Use SPF/DKIM/DMARC tools to help verify the sender
- Implement “External Sender” Banners to notify the reader
- Use Cloud Monitoring tools to monitor for unexpected changes (e.g. password change, mail forwarding, odd login locations, etc.)
Why Awareness Is Key
Masked domains are particularly dangerous because they exploit trust and look very convincing. By staying informed about these tactics and understanding how to identify suspicious domains, you can significantly reduce your risk of falling victim to scams.
We urge our clients and the public to carefully inspect web addresses, especially when they relate to financial or personal information. If you ever receive communication seemingly from us or our partners, please ensure that the domain is legitimate by checking our official website or contacting our support team directly.
Don’t hesitate to get in touch with us if you are a client and need assistance confirming a legitimate domain. Alternatively, please reach out if you aren’t a client and would like to learn more about how our Managed IT Services can protect your team.
Stay safe online!

